Microsoft 365 Essentials for Admin Accounts
When it comes to securing Microsoft 365, your administrative accounts are the "keys to the kingdom".
If an attacker gets hold of one, they can get you plastered all over the news like we've seen so often. Not quite the position anyone wants to be reading about over their morning coffee.
And while "researching" about the topic on LinkedIn, I thought this post from Cyber Security News needed to be included.

The problem?
Too many organisations treat admin accounts like any other user.
Over-privileged, over-exposed, under-protected and largely forgotten.
As an industry, we've seen this story play out in real breaches. A single compromised admin account leads to ransomware deployment, mailbox rule abuse and data exfiltration, all in minutes.
This guide will walk you through the Microsoft 365 essentials every organisation should implement to keep admin accounts safe, reduce over-privilege, and limit the blast radius when something goes wrong.
First and foremost.
Phishing-Resistant Multi-Factor Authentication
Probably the most harped on about of the bunch, and for a good reason.
If your admin account is the keys to the kingdom, phishing-resistant MFA is the armoured vault door and without it, you're just leaving the keys under the welcome mat.
Authenticator apps don't make the cut anymore.
Which gives rise to the new generation of security, FIDO2 and certificate-based authentication.
And from your favourite YubiKey distributor.
"Phishing-resistant MFA is multi-factor authentication (MFA) that is immune from attempts to compromise or subvert the authentication process."
Attackers can't phish a key they can't copy.
Now like you, I'm wondering which of the litany of administrative roles in Microsoft are recommended for phishing-resistant MFA.
Looking over the Microsoft docs, they share a short list to make life simple.
- Global Administrator
- Application Administrator
- Authentication Administrator
- Billing Administrator
- Cloud Application Administrator
- Conditional Access Administrator
- Exchange Administrator
- Helpdesk Administrator
- Password Administrator
- Privileged Authentication Administrator
- Privileged Role Administrator
- Security Administrator
- SharePoint Administrator
- User Administrator
And with a Microsoft Entra ID P1 license, follow through to the Conditional Access section and find the button located in the Grant settings.
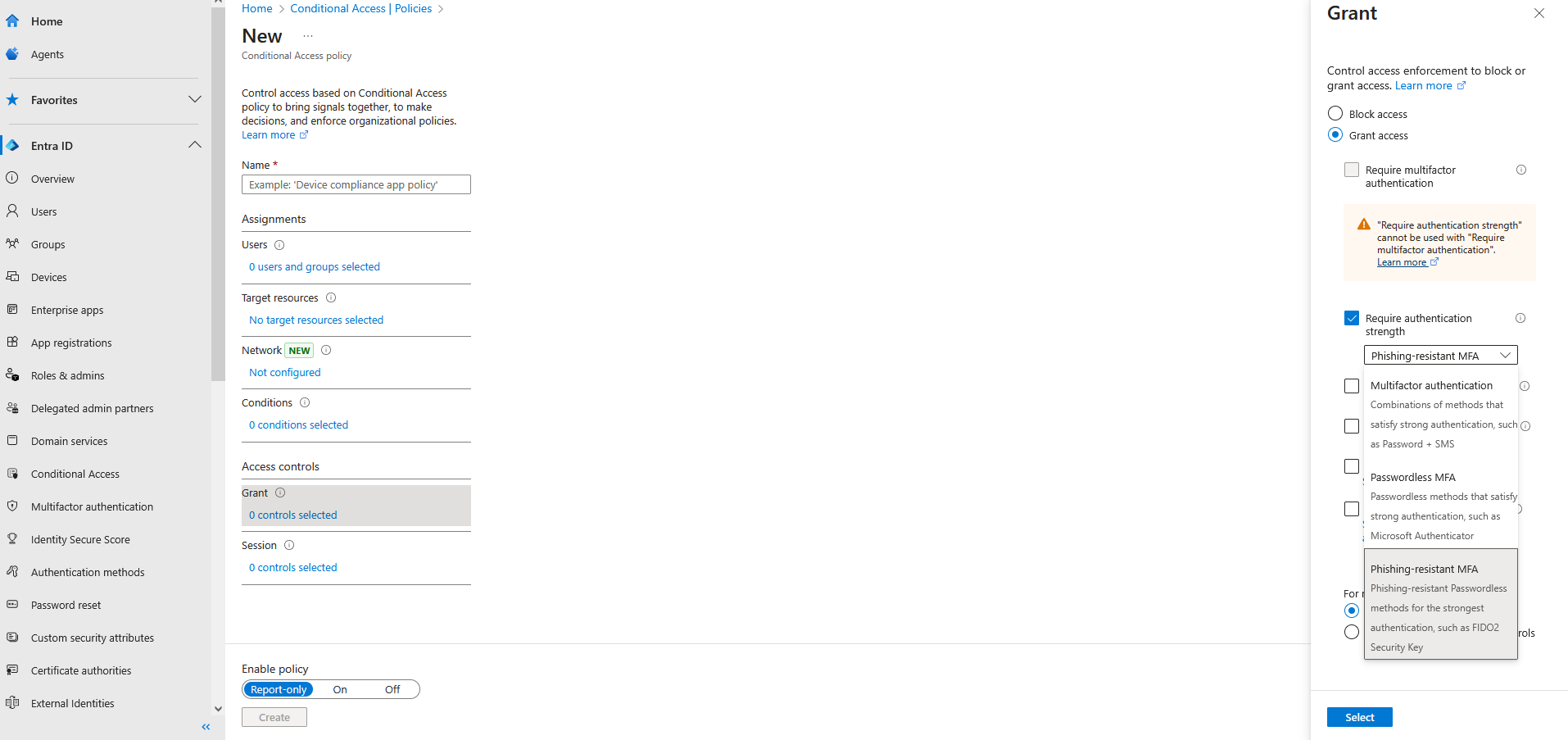
Now with the important one out of the way, there are multiple layers that should be considered before walking away with a job well done.
Global Admin Rights
Global Admin is the "God Mode" of Microsoft 365 and too many people have it. Do they need it? Well. No.
Instead take a page out of the principles of least privilege and go for Role-Based Access Control (RBAC) to assign specific roles as needed for the job that account is required to attend to.
Better yet, remove standing administrative rights entirely and use just-in-time access when needed.
Just-in-Time Access
Pair Microsoft's Privileged Identity Management (PIM) with RBAC to grant elevated rights for a set duration and you have a solid foundation for administrative controls.
The beauty is that when the time's up, the rights go away automatically.
Less standing privilege = smaller attack surface.
Cloud-Only Admin Accounts
If you're running hybrid, it's tempting to sync on-premises admin accounts into Microsoft 365. Don't.
Cloud-only admin accounts break the dependency on potentially compromised Active Directory environments. It's one less entry point for attackers and one more reason you can sleep at night.
Dedicated Admin Accounts
No Mixing Business with Privilege.
Admins should never check email, join Teams meetings, or browse the web with their privileged account. Daily tasks and administrative duties should live in separate accounts.
This single change alone can cut phishing risk dramatically.
All too often organisations grow in maturity and old habits live on with privileged user accounts, even when dedicated ones have been established.
A quick audit of your privileged accounts could save you a major headache.
Break-Glass Accounts
Things break. MFA systems fail. Network outages happen.
That's why you need at least two emergency "break-glass" accounts with Global Administrator rights.
Keep them cloud-only and store credentials in a secure, offline location.
And here's the kicker, test them regularly. The worst time to find out your emergency access doesn't work… is during an emergency.
Log and Monitor Administrative Activity
Turn on Unified Audit Logs and watch them like a hawk.
Flag high-risk patterns such as:
- Sign-ins from unfamiliar countries
- Impossible travel events (two sign-ins from opposite sides of the globe minutes apart)
- Repeated failed MFA attempts
Better yet, integrate logs into a SIEM or MDR service for real-time alerts.
Strong Password Policy
Even with MFA, a weak password is a problem.
Require long passwords, ban known-breached ones and enforce lockouts for repeated failures.
To simplify passwords, just use a passphrase generator.

And no, just because the generate passphrases does it mean they store them and could somehow compromise your account.
Easy to remember and doesn't need to be 42 characters long.
Remove Application Licenses from Admin Accounts
If your admin account doesn't have Outlook, Teams, or SharePoint access, attackers can't use those services to phish or spread malware.
No license = no inbox = no spear phishing.
Privilege is a Liability
Every admin account is a potential breach path.
By tightening privileges, enforcing strong authentication, and removing unnecessary access, you dramatically reduce the risk of an attacker turning one account into total compromise.
The key is taking the steps towards implementing these measures across your environment.
Start with the most critical ones like phishing-resistant MFA and work your way through the list. Your admin accounts will thank you, and so will your security team.
